As an important part of the emergency communication network, the command information network carries key business applications such as emergency command and rescue, big data analysis, video conference and partial monitoring and early warning, and is securely connected with the national e-government external network and the Internet. How to build a sufficiently safe command information network to prevent damage and attack by hostile forces and lawbreakers has become the top priority of Taiyuan Emergency Management Bureau in the construction of command information network.
Faced with such a critical business security task, Taiyuan Emergency Management Bureau carried out the construction of network security system through three measures to effectively guarantee the security of the command information network.
Based on behavior analysis technology, DDP can easily cope with unknown threat scenarios
The RG-DDP dynamic attack defense system is used to locate Intranet security and create dynamic and random changing Intranet environment to improve Intranet security. Different from other security devices, Ruijie DDP does not need to rely on the signature database, and creates a large number of decoy terminals in the network to deceive the attacker. When the attacker or poisoned terminal initiates detection or attacks (port scanning, IP detection, flooding attack, ARP spoofing, etc.), RG-DDP can directly alarm or even block as long as it touches virtual machines or open ports. Fully and effectively defend against, identify and locate known and unknown attacks, including APT attacks, trojans, worms and viruses, to prevent the spread of attacks across the network.
Security resource pools are deployed and on-demand allocation reduces construction costs
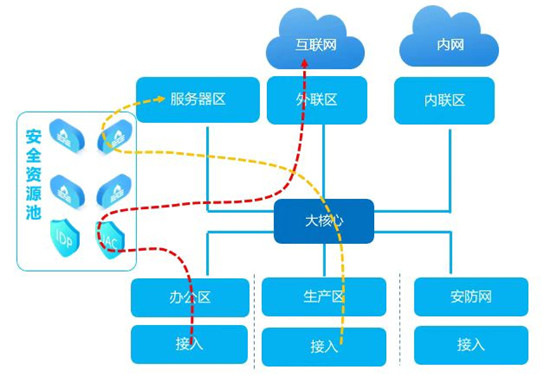
Deploy ServiceChain based on SDN technology, innovatively adopt on-demand drainage, no network, continuous network and other methods, and use SDN controller to redefine the deployment mode of security devices. There is no need to deploy physical devices directly at the boundary of the area to realize logical isolation and improve the reuse rate of security devices. Flexibly design traffic paths based on different service requirements and assign them to appropriate security devices; Realize cross-brand load balancing, easily upgrade the network; Change the deployment mode of export "sugar gourd string", no longer exist single point of failure risk. The secure elastic network created by ServiceChain greatly reduces the construction cost on the basis of ensuring link redundancy.
Adopt Ruijie equal protection 2.0 scheme and pass the three level evaluation of equal protection
According to the "People's Republic of China Network Security Law" "Information security technology network security level protection basic requirements" (GB/T 22239-2019 instead of GB/T 22239-2008) "Emergency Management Informatization Development Strategic Planning Framework (2018-2022)" and "The Ministry of Emergency Management of Science, Technology and Informatization Leading Group Office on the issuance of Local Emergency Management Informatization 2020 construction Task Book" and other construction requirements, directed the information network to start the construction of information security level protection. Using Ruijieet protection 2.0 solution, according to the concept of "one center, three defense", the deployment of security gateway EG, dynamic attack protection system DDP, database audit DBS, log analysis BDS, leak SCAN, fortress machine OAS, behavior audit UAC, intrusion detection IDP, website protection WG and firewall and other related security products. Completed the Level 3 construction and passed the evaluation smoothly